Back to ConfigMgr main menu
This post will include issues I've encountered while deploying ConfigMgr 2012 for customers.They are in random order but I hope they can help others when they are in difficulty. I will add to the post as I encounter further issues worth mentioning.
ConfigMgr 2012 DP - The self signed certificate could not be created for DP
ConfigMgr 2012 - Reports not running
ConfigMgr 2012 and McAfee
ConfigMgr 2012 - create new boot images
ConfigMgr 2012 / SCCM 2012 Task Sequence fails with BCD error
OSD Task Sequence fails on preparing network connections in Windows PE
Failed to sync update. Error The Microsoft Software License Terms have not been completely downloaded and cannot be accepted
Windows Intune Setup: The software cannot be installed, 0x800b0101
WSUS Service will not start Error 193: 0xc1
ConfigMgr 2012/1E Nomad - Downloading (0% complete)
Alternate Login IDs cannot be used with ConfigMgr 2012 and Windows Intune
Installing Configuration Manager - Visual Studio Invalid license data. Reinstall is required
Friday 28 February 2014
ConfigMgr 2012 - create new boot images
Back to ConfigMgr main menu
On occasions it can be necessary to create your own boot images to import to ConfigMgr. You do this using DISM, which is part of the Microsoft Assessment and Deployment Kit.
Niall Brady has a good blog on this process:
http://www.niallbrady.com/2013/10/09/how-can-i-manually-add-winpe-5-boot-images-to-system-center-2012-configuration-manager-sp1-cu3/
Also, have a look at this article by Kenneth van Surksum.
http://myitforum.com/myitforumwp/2013/08/01/how-to-create-configmgr-2012-boot-images-from-scratch/
Beware. Disable McAfee services before you start.
Also, ensure that you are using the correct version of DISM.
On occasions it can be necessary to create your own boot images to import to ConfigMgr. You do this using DISM, which is part of the Microsoft Assessment and Deployment Kit.
Niall Brady has a good blog on this process:
http://www.niallbrady.com/2013/10/09/how-can-i-manually-add-winpe-5-boot-images-to-system-center-2012-configuration-manager-sp1-cu3/
Also, have a look at this article by Kenneth van Surksum.
http://myitforum.com/myitforumwp/2013/08/01/how-to-create-configmgr-2012-boot-images-from-scratch/
Beware. Disable McAfee services before you start.
Also, ensure that you are using the correct version of DISM.
ConfigMgr 2012 and McAfee
Back to ConfigMgr main menu
ConfigMgr 2012 and McAfee VirusScan do not play nicely together. The main reason is that McAfee cannot handle DISM. This is well documented and available on the McAfee website.
https://kc.mcafee.com/corporate/index?page=content&id=KB76867&actp=LIST
So what problems can this cause
1. Boot images are not created during ConfigMgr installation. This is a real pain.
2. You cannot use DISM to manually create the boot images - you get access denied error.
3. You cannot add drivers to the boot image. The process fails as it uses DISM.
The solution is to disable both Access Protection and On-Access Scanner before you carry out any of these tasks. You can enable them again afterwards.
This is the official guidance from McAfee - see the link above.
ConfigMgr 2012 and McAfee VirusScan do not play nicely together. The main reason is that McAfee cannot handle DISM. This is well documented and available on the McAfee website.
https://kc.mcafee.com/corporate/index?page=content&id=KB76867&actp=LIST
So what problems can this cause
1. Boot images are not created during ConfigMgr installation. This is a real pain.
2. You cannot use DISM to manually create the boot images - you get access denied error.
3. You cannot add drivers to the boot image. The process fails as it uses DISM.
The solution is to disable both Access Protection and On-Access Scanner before you carry out any of these tasks. You can enable them again afterwards.
This is the official guidance from McAfee - see the link above.
ConfigMgr 2012 - Reports not running
Back to ConfigMgr main menu
After installing ConfigMgr 2012 at a customer site I encountered an odd problem. I had just added the Reporting Services Point and all looked normal. The reports were available in the ConfigMgr console and in SQL Server Reporting Services. I could right click on a report but nothing happened when I tried to run it - no error, nothing.
After some troubleshooting I noticed that Report Viewer had not been installed during the installation.
Double clicked on ReportViewer.exe
Started the installation of MS Report Viewer 2010 SP1
Then I could run my reports
After installing ConfigMgr 2012 at a customer site I encountered an odd problem. I had just added the Reporting Services Point and all looked normal. The reports were available in the ConfigMgr console and in SQL Server Reporting Services. I could right click on a report but nothing happened when I tried to run it - no error, nothing.
After some troubleshooting I noticed that Report Viewer had not been installed during the installation.
I navigated to "C:\Program
Files (x86)\Microsoft Configuration Manager\AdminConsole\bin"
Double clicked on ReportViewer.exe
Started the installation of MS Report Viewer 2010 SP1
Then I could run my reports
ConfigMgr 2012 DP - The self signed certificate could not be created successfully
Back to ConfigMgr main menu
I was working on a new customer deployment of ConfigMgr 2012 - single primary site server with Management Point and Distribution Point selected during the installation.
Everything looked normal and all component status were green. However I had an issue with software distribution. When I looked at the status of the deployment I saw that the deployment was "waiting for content".
That would suggest a problem with the DP. I looked at the properties and found this error.
It looks like the self-signed certificate for the DP was not created during the installation. I tried to apply the settings but got this error.
I couldn't quite figure this out. I restarted the server and logged in again. This time I noticed that icons that I had placed on the desktop had disappeared. I did a little digging and found that I had been logged on using a temporary profile - I was using an account provided by the customer.
When creating certificates full access to save to your profile is required. Once I realized the problem I was able to solve the user profile issue. The next time I logged on to the server I was able to create the certificate.
I was working on a new customer deployment of ConfigMgr 2012 - single primary site server with Management Point and Distribution Point selected during the installation.
Everything looked normal and all component status were green. However I had an issue with software distribution. When I looked at the status of the deployment I saw that the deployment was "waiting for content".
That would suggest a problem with the DP. I looked at the properties and found this error.
It looks like the self-signed certificate for the DP was not created during the installation. I tried to apply the settings but got this error.
I couldn't quite figure this out. I restarted the server and logged in again. This time I noticed that icons that I had placed on the desktop had disappeared. I did a little digging and found that I had been logged on using a temporary profile - I was using an account provided by the customer.
When creating certificates full access to save to your profile is required. Once I realized the problem I was able to solve the user profile issue. The next time I logged on to the server I was able to create the certificate.
Monday 3 February 2014
MDM in SCCM 2012 R2 - Upcoming New Features
Back to ConfigMgr main menu
Back to MDM Menu
Recently Microsoft announced upcoming new features in the Mobile Device Management offering. They have committed to releasing these improvements very regularly and not just coinciding with a new release or update to ConfigMgr.
To facilitate these updates they have introduced a new feature with ConfigMgr 2012 R2 - "Extensions for Windows Intune".
This enables new features in Windows Intune to be available within your ConfigMgr console without any on-premise upgrade. Administrators will be prompted with a message to notify them about the availability of a new extension. The administrator can then choose to install the extension.
After the installation (and after a restart of the console) the new feature will be available in the workspace.
(Note that additional features will be automatically replicated and enabled on all site servers in the Configuration Manager hierarchy of servers.)
You can read about this in the System Center Configuration Manager Team Blog (29th Jan 2014).
https://blogs.technet.com/b/configmgrteam/archive/2014/01/29/provision-activesync-email-profiles-to-mobile-devices-using-configmgr-and-windows-intune.aspx
The following features will soon be available as Extensions for Windows Intune (week commencing 3rd Feb 2014)
Email profiles:
Later in 2014
Back to MDM Menu
Recently Microsoft announced upcoming new features in the Mobile Device Management offering. They have committed to releasing these improvements very regularly and not just coinciding with a new release or update to ConfigMgr.
To facilitate these updates they have introduced a new feature with ConfigMgr 2012 R2 - "Extensions for Windows Intune".
This enables new features in Windows Intune to be available within your ConfigMgr console without any on-premise upgrade. Administrators will be prompted with a message to notify them about the availability of a new extension. The administrator can then choose to install the extension.
After the installation (and after a restart of the console) the new feature will be available in the workspace.
(Note that additional features will be automatically replicated and enabled on all site servers in the Configuration Manager hierarchy of servers.)
You can read about this in the System Center Configuration Manager Team Blog (29th Jan 2014).
https://blogs.technet.com/b/configmgrteam/archive/2014/01/29/provision-activesync-email-profiles-to-mobile-devices-using-configmgr-and-windows-intune.aspx
The following features will soon be available as Extensions for Windows Intune (week commencing 3rd Feb 2014)
Email profiles:
- provision ‘Exchange ActiveSync’ email profiles to iOS and Windows Phone 8 devices
- allows the enforcement of email-related restrictions
- remove the profile and emails associated with that profile from wiped devices
- lets admins lock-down employee tablets, phones, and other mobile devices that are lost or stolen
- "Managed open in" capability to protect corporate data by controlling which apps and accounts are used to open documents and attachments
- disabling the "fingerprint unlock" feature.
Later in 2014
- Deeper email management, including conditional access to Exchange email inboxes depending on if the device is managed
- Ability to define application restrictions, through direct platform management as well as “wrapping” policy around unmanaged applications, giving administrators the ability to define how an application interacts with data and block undesirable functions such as cut and paste to other apps
- Bulk enrollment of mobile devices, specifically useful for devices not used by a single user or knowledge worker, including kiosks, student devices, or those used in retail
- Allow or deny apps from running on mobile devices
- Web browser management, including URL filtering to manage which web sites mobile devices can access
MDM in SCCM 2012 R2 - Troubleshooting
Back to ConfigMgr main menu
Back to MDM Menu
As you will be aware ConfigMgr 2012 R2 provides very extensive logging to aid in troubleshooting. Log files are provided for every step of the MDM process. You just need to know where to look.
What is the problem?
You cannot enrol any device - you clearly have a global problem. Have you created the subscription and connector correctly?
You cannot enrol iOS devices - verify your APN.
You cannot enrol Windows 8 Phones - verify your code signing certificate and signed company app.
You cannot enrol any device with a specific user - verify the users UPN and that it has synchronized with Intune. Verify that the user has been discovered by ConfigMgr and that you have added them to the "Intune Users" collection.
The process is as follows:
1. Intune Subscription and Connector
Review the sitecomp.log file. Verify that the "CloudUserSync" site component has been created without error.
2. Configure UPN and sync AD users with Intune
Browse to the DirSync folder and launch miisclient.exe as Administrator
(C:\Program Files\Windows Azure Active Directory Sync\SYNCBUS\Synchronization Service\UIShell\miisclient.exe)
Right click the Active Directory Connector and choose Run.
Choose "Full Import Full Sync".
Verify success of the sync. Click on "Updates".
Verify the change you require.
Note that DirSync synchronises with Azure every 3 hours by default. You can run it manually using the procedure above as often as you require (eg. you have added a new user, changed a password or added a UPN).
3. Discover AD Users
Review the adusrdis.log file. Verify that Data Discovery Records (DDRs) are created for your users.
4. Add user to Intune User collection
Adding a user to the Intune Users collection allows that user to enrol mobile devices. When you add a user to the collection check in the console to verify that it was actually added. You may have to right click on the collection to "Update Membership".
If you do not want to wait for the scheduled syncronization with Intune you can force the sync by restarting the "CloudUserSync" site component.
Right click on any site component and choose to start the Configuration Manager Service Manager.
Right click on the SMS_CLOUD_USERSYNC component and select Query.
You will see that the component is running. Right click again and choose to stop it
Reverse the process to start it again.
(Note that restarting the server has the same effect but that's a little extreme.)
Verify that your change was successful using the cloudusersync.log file.
5. Enrol devices
Check the Dmpuploader.log to verify the connector site system role is able upload policy etc. to the Windows Intune Service.
Check the Dmpdownloader.log to verify that the connector is able to download messages from Windows Intune. Note: this log might only show a ping at the beginning, there might be no messages created for download initially.
6. Exchange Connector
Verify success or failure using the EasDisc.log file.
Back to MDM Menu
As you will be aware ConfigMgr 2012 R2 provides very extensive logging to aid in troubleshooting. Log files are provided for every step of the MDM process. You just need to know where to look.
What is the problem?
You cannot enrol any device - you clearly have a global problem. Have you created the subscription and connector correctly?
You cannot enrol iOS devices - verify your APN.
You cannot enrol Windows 8 Phones - verify your code signing certificate and signed company app.
You cannot enrol any device with a specific user - verify the users UPN and that it has synchronized with Intune. Verify that the user has been discovered by ConfigMgr and that you have added them to the "Intune Users" collection.
The process is as follows:
1. Intune Subscription and Connector
Review the sitecomp.log file. Verify that the "CloudUserSync" site component has been created without error.
2. Configure UPN and sync AD users with Intune
Browse to the DirSync folder and launch miisclient.exe as Administrator
(C:\Program Files\Windows Azure Active Directory Sync\SYNCBUS\Synchronization Service\UIShell\miisclient.exe)
Right click the Active Directory Connector and choose Run.
Choose "Full Import Full Sync".
Verify success of the sync. Click on "Updates".
Verify the change you require.
Note that DirSync synchronises with Azure every 3 hours by default. You can run it manually using the procedure above as often as you require (eg. you have added a new user, changed a password or added a UPN).
3. Discover AD Users
Review the adusrdis.log file. Verify that Data Discovery Records (DDRs) are created for your users.
4. Add user to Intune User collection
Adding a user to the Intune Users collection allows that user to enrol mobile devices. When you add a user to the collection check in the console to verify that it was actually added. You may have to right click on the collection to "Update Membership".
If you do not want to wait for the scheduled syncronization with Intune you can force the sync by restarting the "CloudUserSync" site component.
Right click on any site component and choose to start the Configuration Manager Service Manager.
Right click on the SMS_CLOUD_USERSYNC component and select Query.
You will see that the component is running. Right click again and choose to stop it
Reverse the process to start it again.
(Note that restarting the server has the same effect but that's a little extreme.)
Verify that your change was successful using the cloudusersync.log file.
5. Enrol devices
Check the Dmpuploader.log to verify the connector site system role is able upload policy etc. to the Windows Intune Service.
Check the Dmpdownloader.log to verify that the connector is able to download messages from Windows Intune. Note: this log might only show a ping at the beginning, there might be no messages created for download initially.
6. Exchange Connector
Verify success or failure using the EasDisc.log file.
MDM in SCCM 2012 R2 - Device Ownership (Company or Personal)
Back to ConfigMgr main menu
Back to MDM Menu
Devices enrolled using the ConfigMgr 2012/Windows Intune unified solution can be managed in the ConfigMgr console. These devices can be assigned to be either "Company" or "Personal" devices. Note that a device is automatically assigned to be Personal by default.
What is the difference - Company V Personal?
Inventory: Company devices will report all hardware and software information. For Personal devices, only software installed by the unified solution is reported.
Software Distribution: You can target software or compliance settings to devices based on ownership. This is achieved using Global Conditions.
Right click a device to change the ownership
Select "Change Ownership".
Select your preference. If you do not configure this your devices will be Personal. Note that you can highlight several devices together and configure this attribute.
Selective Wipe
"Selective Wipe" is a new feature with ConfgMgr 2012 R2. Selective Wipe removes only the corporate data and applications that are deployed by using Configuration Manager. All photos, videos and other personal files on the user’s device are left intact.
You can still carry out a "Full Wipe". All the data on the device is deleted. This includes all personal data - photos, videos, personal emails, and applications installed from the public store by the user.
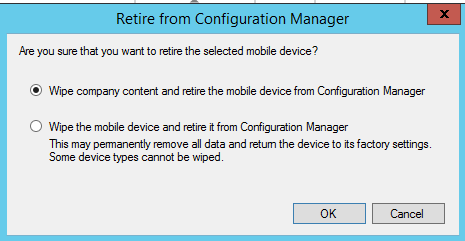
Right click a device to retire or wipe it.
Choose "Retire/Wipe" (this option is not available if you choose multiple devices).
Select your option.
Read and accept the Warning.
Note the different features of Full and Selective Wipe.
Note the company content that is removed by a Selective Wipe.
Back to MDM Menu
Devices enrolled using the ConfigMgr 2012/Windows Intune unified solution can be managed in the ConfigMgr console. These devices can be assigned to be either "Company" or "Personal" devices. Note that a device is automatically assigned to be Personal by default.
What is the difference - Company V Personal?
Inventory: Company devices will report all hardware and software information. For Personal devices, only software installed by the unified solution is reported.
Software Distribution: You can target software or compliance settings to devices based on ownership. This is achieved using Global Conditions.
Right click a device to change the ownership
Select "Change Ownership".
Select your preference. If you do not configure this your devices will be Personal. Note that you can highlight several devices together and configure this attribute.
Selective Wipe
"Selective Wipe" is a new feature with ConfgMgr 2012 R2. Selective Wipe removes only the corporate data and applications that are deployed by using Configuration Manager. All photos, videos and other personal files on the user’s device are left intact.
You can still carry out a "Full Wipe". All the data on the device is deleted. This includes all personal data - photos, videos, personal emails, and applications installed from the public store by the user.
Right click a device to retire or wipe it.
Select your option.
Read and accept the Warning.
Note the different features of Full and Selective Wipe.
Note the company content that is removed by a Selective Wipe.
Subscribe to:
Posts (Atom)